
Integrate SonarQube into Pipelines
SonarQube is a popular continuous inspection tool for code quality. You can use it for static and dynamic analysis of a codebase. After it is integrated into pipelines in KubeSphere Container Platform, you can view common code issues such as bugs and vulnerabilities directly on the dashboard as SonarQube detects issues in a running pipeline.
This tutorial demonstrates how you can integrate SonarQube into pipelines. Refer to the following steps first before you create a pipeline using a Jenkinsfile.
Prerequisites
You need to enable the KubeSphere DevOps System.
Install the SonarQube Server
To integrate SonarQube into your pipeline, you must install SonarQube Server first.
Install Helm first so that you can install SonarQube using the tool. For example, run the following command to install Helm 3:
curl https://raw.githubusercontent.com/helm/helm/master/scripts/get-helm-3 | bashView the Helm version.
helm version version.BuildInfo{Version:"v3.4.1", GitCommit:"c4e74854886b2efe3321e185578e6db9be0a6e29", GitTreeState:"clean", GoVersion:"go1.14.11"}Note
For more information, see the Helm documentation.Execute the following command to install SonarQube Server.
helm upgrade --install sonarqube sonarqube --repo https://charts.kubesphere.io/main -n kubesphere-devops-system --create-namespace --set service.type=NodePortNote
Make sure you use Helm 3 to install SonarQube Server.You will get this prompt:
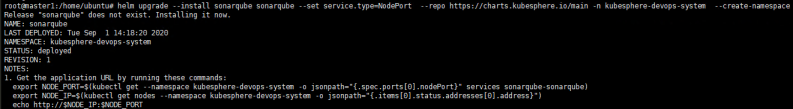
Get the SonarQube Console Address
Execute the following command to get SonarQube NodePort.
export NODE_PORT=$(kubectl get --namespace kubesphere-devops-system -o jsonpath="{.spec.ports[0].nodePort}" services sonarqube-sonarqube) export NODE_IP=$(kubectl get nodes --namespace kubesphere-devops-system -o jsonpath="{.items[0].status.addresses[0].address}") echo http://$NODE_IP:$NODE_PORTYou can get the output as below (
31434is the port number in this example, which may be different from yours):http://192.168.0.4:31434
Configure the SonarQube Server
Step 1: Access the SonarQube console
Execute the following command to view the status of SonarQube. Note that the SonarQube console is not accessible until SonarQube is up and running.
$ kubectl get pod -n kubesphere-devops-system NAME READY STATUS RESTARTS AGE devops-jenkins-68b8949bb-7zwg4 1/1 Running 0 84m s2ioperator-0 1/1 Running 1 84m sonarqube-postgresql-0 1/1 Running 0 5m31s sonarqube-sonarqube-bb595d88b-97594 1/1 Running 2 5m31sAccess the SonarQube console
http://<Node IP>:<NodePort>in your browser.Click Log in in the upper-right corner and log in as the default account
admin/admin.Note
You may need to set up necessary port forwarding rules and open the port to access SonarQube in your security groups depending on where your instances are deployed.
Step 2: Create a SonarQube admin token
Click the letter A and select My Account from the menu to go to the Profile page.
Click Security and enter a token name, such as
kubesphere.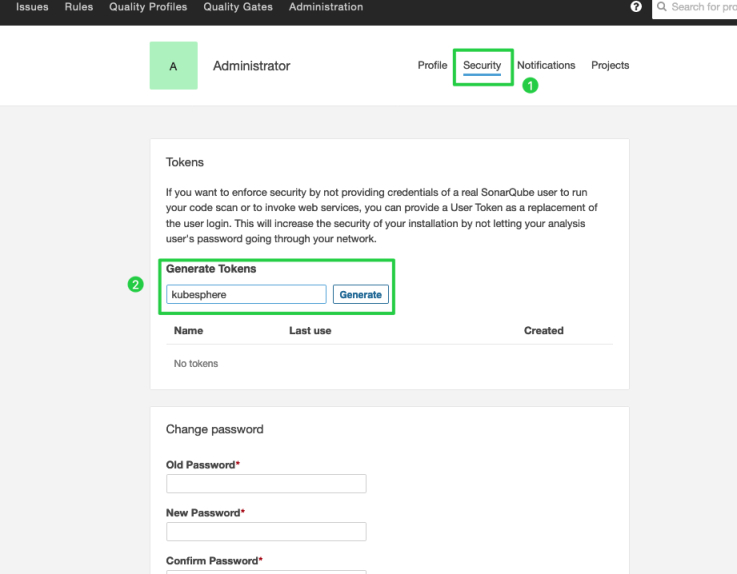
Click Generate and copy the token.
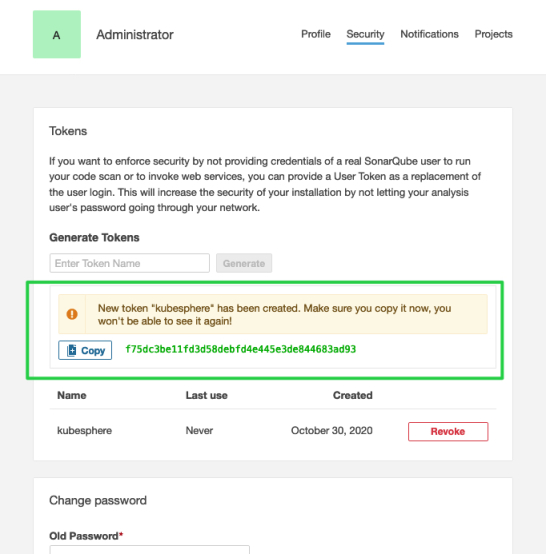
Warning
Make sure you do copy the token because you won't be able to see it again as shown in the prompt.
Step 3: Create a webhook server
Execute the following command to get the address of SonarQube Webhook.
export NODE_PORT=$(kubectl get --namespace kubesphere-devops-system -o jsonpath="{.spec.ports[0].nodePort}" services devops-jenkins) export NODE_IP=$(kubectl get nodes --namespace kubesphere-devops-system -o jsonpath="{.items[0].status.addresses[0].address}") echo http://$NODE_IP:$NODE_PORT/sonarqube-webhook/Expected output:
http://192.168.0.4:30180/sonarqube-webhook/Click Administration, Configuration and Webhooks in turn to create a webhook.
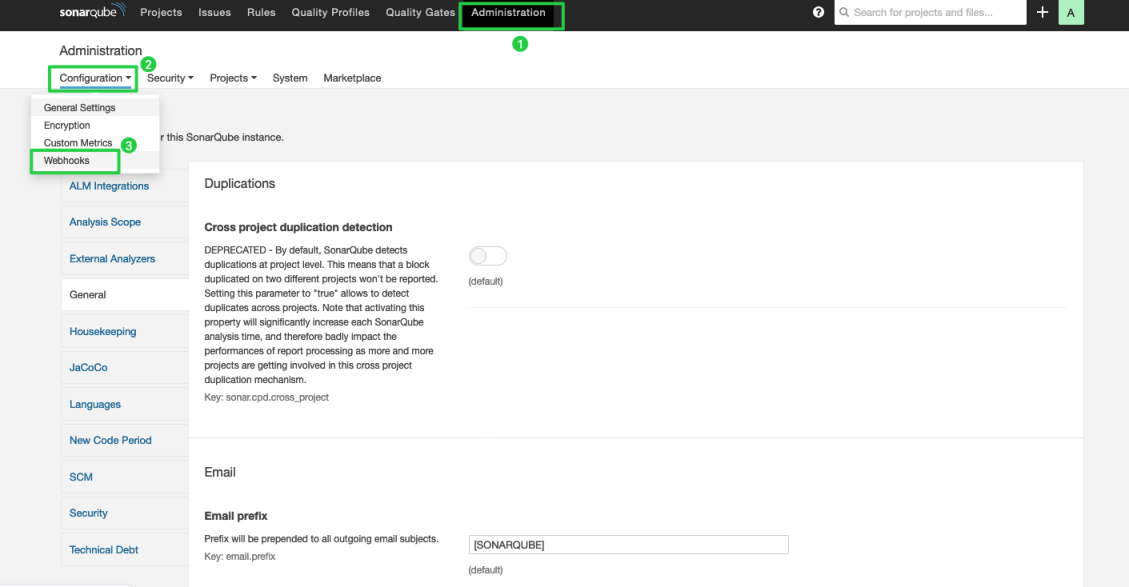
Click Create.
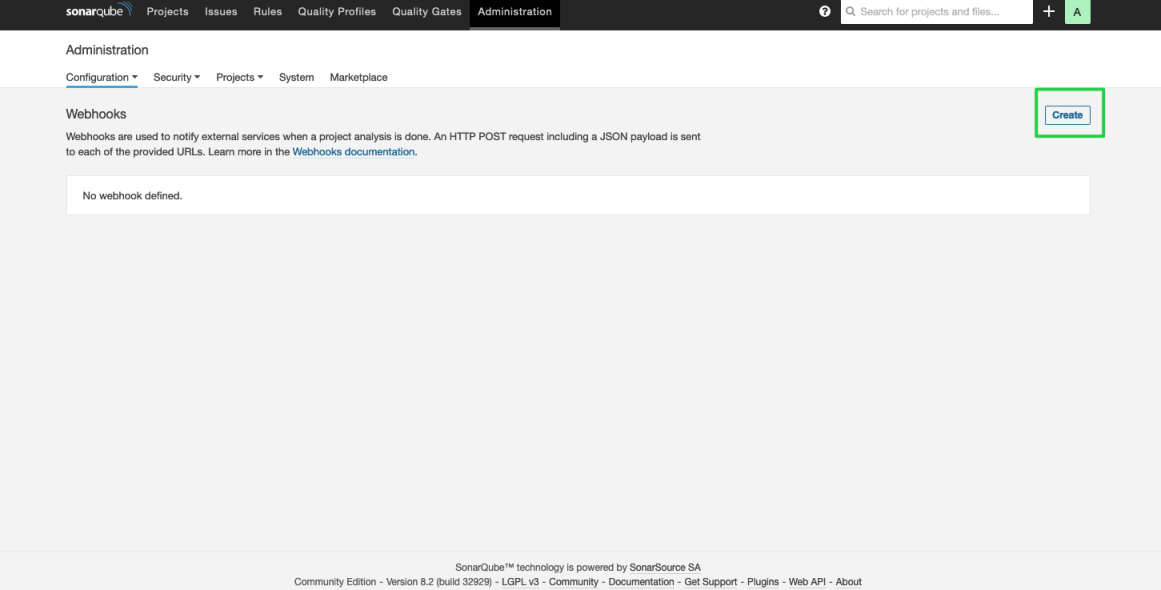
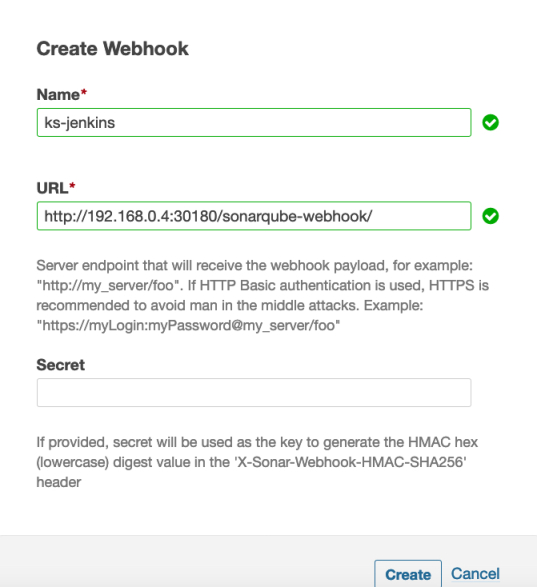
Enter Name and Jenkins Console URL (for example, the SonarQube Webhook address) in the displayed dialog box. Click Create to finish.
Step 4: Add the SonarQube configuration to ks-installer
Execute the following command to edit
ks-installer.kubectl edit cc -n kubesphere-system ks-installerNavigate to
devops. Add the fieldsonarqubeand specifyexternalSonarUrlandexternalSonarTokenunder it.devops: enabled: true jenkinsJavaOpts_MaxRAM: 2g jenkinsJavaOpts_Xms: 512m jenkinsJavaOpts_Xmx: 512m jenkinsMemoryLim: 2Gi jenkinsMemoryReq: 1500Mi jenkinsVolumeSize: 8Gi sonarqube: # Add this field manually. externalSonarUrl: http://192.168.0.4:31434 # The SonarQube IP address. externalSonarToken: f75dc3be11fd3d58debfd4e445e3de844683ad93 # The SonarQube admin token created above.Save the file after you finish.
Step 5: Add the SonarQube server to Jenkins
Execute the following command to get the address of Jenkins.
export NODE_PORT=$(kubectl get --namespace kubesphere-devops-system -o jsonpath="{.spec.ports[0].nodePort}" services devops-jenkins) export NODE_IP=$(kubectl get nodes --namespace kubesphere-devops-system -o jsonpath="{.items[0].status.addresses[0].address}") echo http://$NODE_IP:$NODE_PORTYou can get the output as below, which tells you the port number of Jenkins.
http://192.168.0.4:30180Access Jenkins with the address
http://<Node IP>:30180. When KubeSphere is installed, the Jenkins dashboard is also installed by default. Besides, Jenkins is configured with KubeSphere LDAP, which means you can log in to Jenkins with KubeSphere accounts (for example,admin/P@88w0rd) directly. For more information about configuring Jenkins, see Jenkins System Settings.Note
You may need to set up necessary port forwarding rules and open port30180to access Jenkins in your security groups depending on where your instances are deployed.Click Manage Jenkins on the left navigation pane.
Scroll down to Configure System and click it.
Navigate to SonarQube servers and click Add SonarQube.
Enter Name and Server URL (
http://<Node IP>:<NodePort>). Click Add, select Jenkins, and then create the credentials with the SonarQube admin token in the displayed dialog box as shown in the second image below. After adding the credentials, select it from the drop-down list for Server authentication token and then click Apply to finish.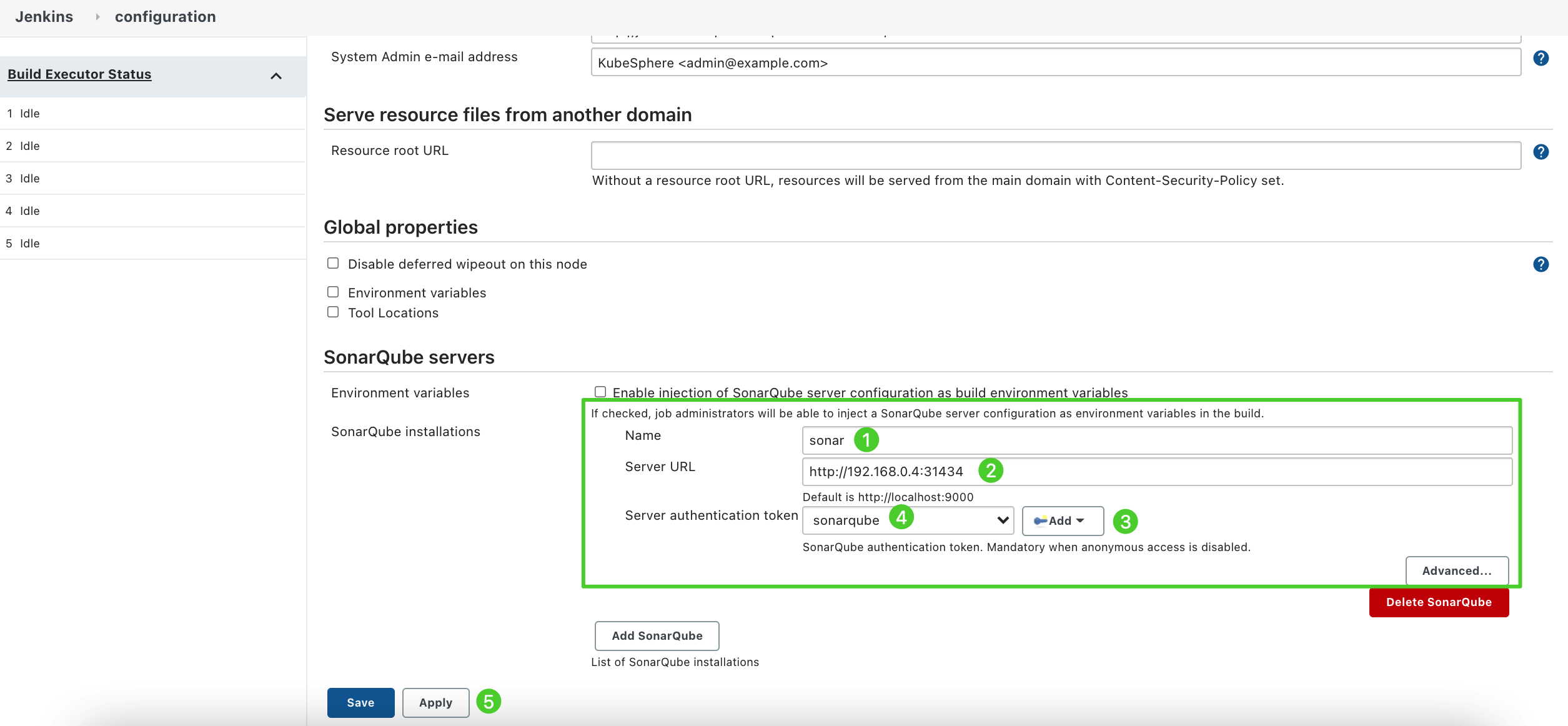
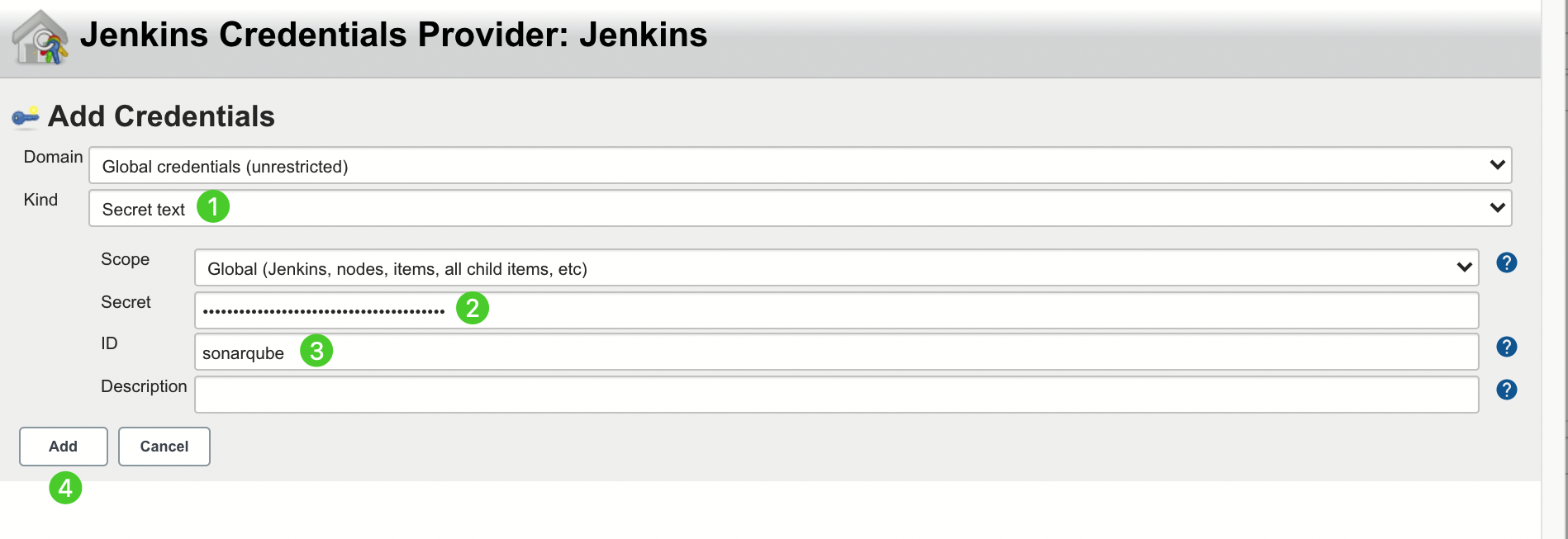
Note
If the Add button is not working, which is a known bug from Jenkins, you can navigate to Manage Credentials under Manage Jenkins, click Jenkins under Stores scoped to Jenkins, click Global credentials (unrestricted), and then click Add Credentials from the left navigation bar to add the credentials with the SonarQube admin token by referencing the second image above. After you add the credentials, you can select it from the drop-down list for Server authentication token.
Step 6: Add sonarqubeURL to the KubeSphere Console
You need to specify sonarqubeURL so that you can access SonarQube directly from the KubeSphere console.
Execute the following command:
kubectl edit cm -n kubesphere-system ks-console-configGo to
data.client.enableKubeConfigand add the fielddevopswithsonarqubeURLspecified under it.client: enableKubeConfig: true devops: # Add this field manually. sonarqubeURL: http://192.168.0.4:31434 # The SonarQube IP address.Save the file.
Step 7: Restart Services
Execute the following commands.
kubectl -n kubesphere-devops-system rollout restart deploy devops-apiserver
kubectl -n kubesphere-system rollout restart deploy ks-console
Create a SonarQube Token for a New Project
You need a SonarQube token so that your pipeline can communicate with SonarQube as it runs.
On the SonarQube console, click Create new project.
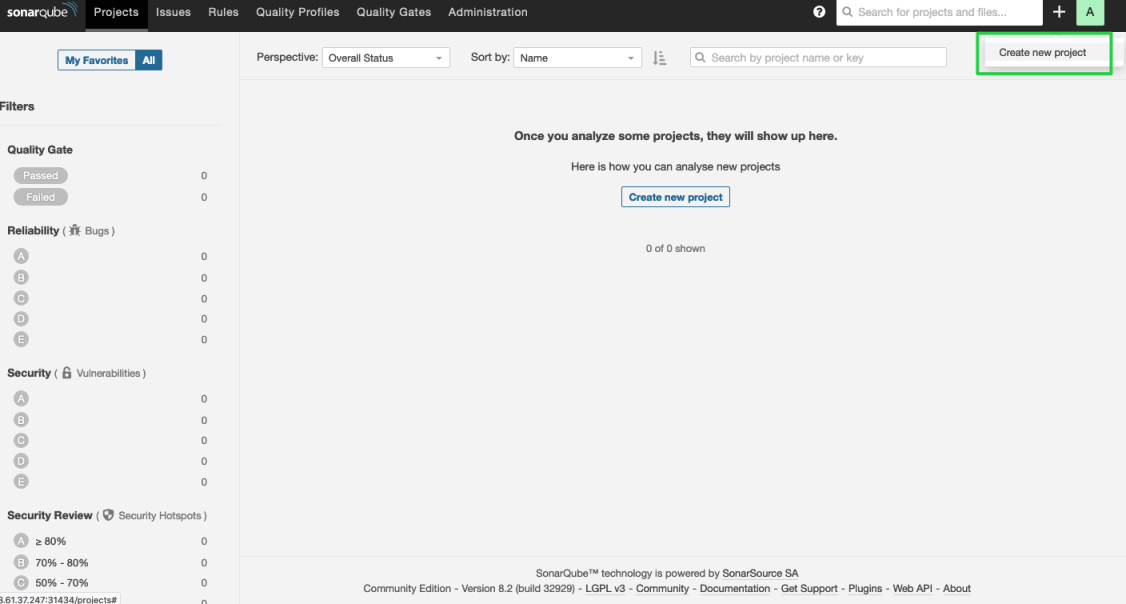
Enter a project key, such as
java-demo, and click Set Up.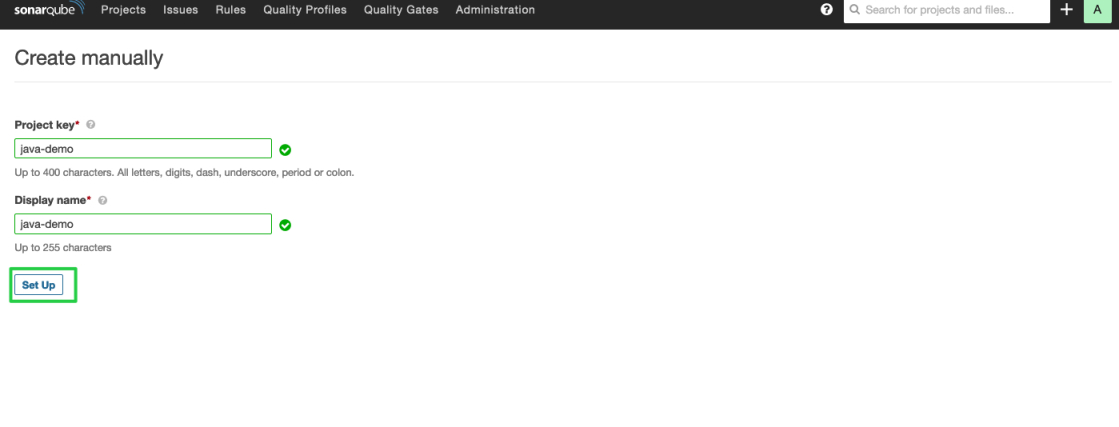
Enter a project name, such as
java-sample, and click Generate.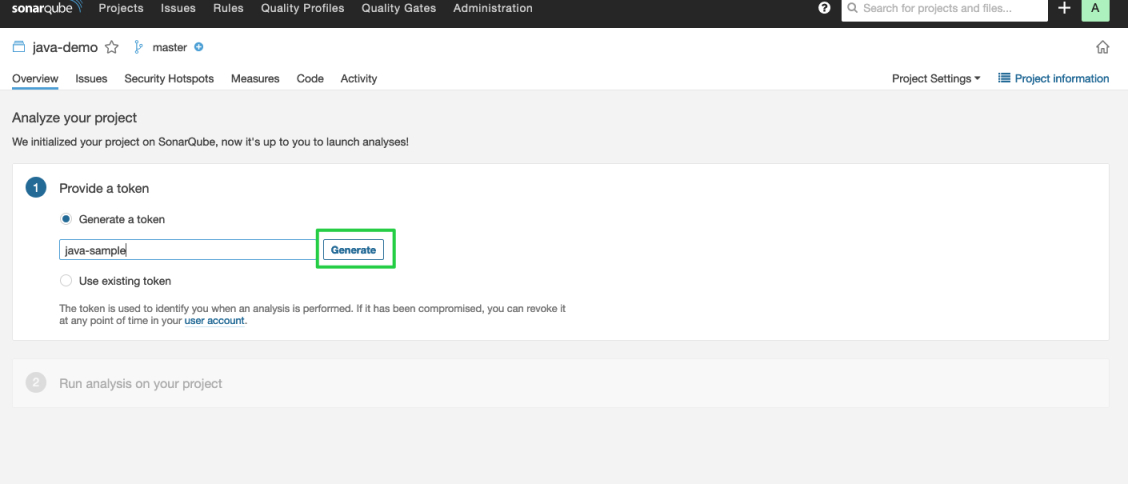
After the token is created, click Continue.
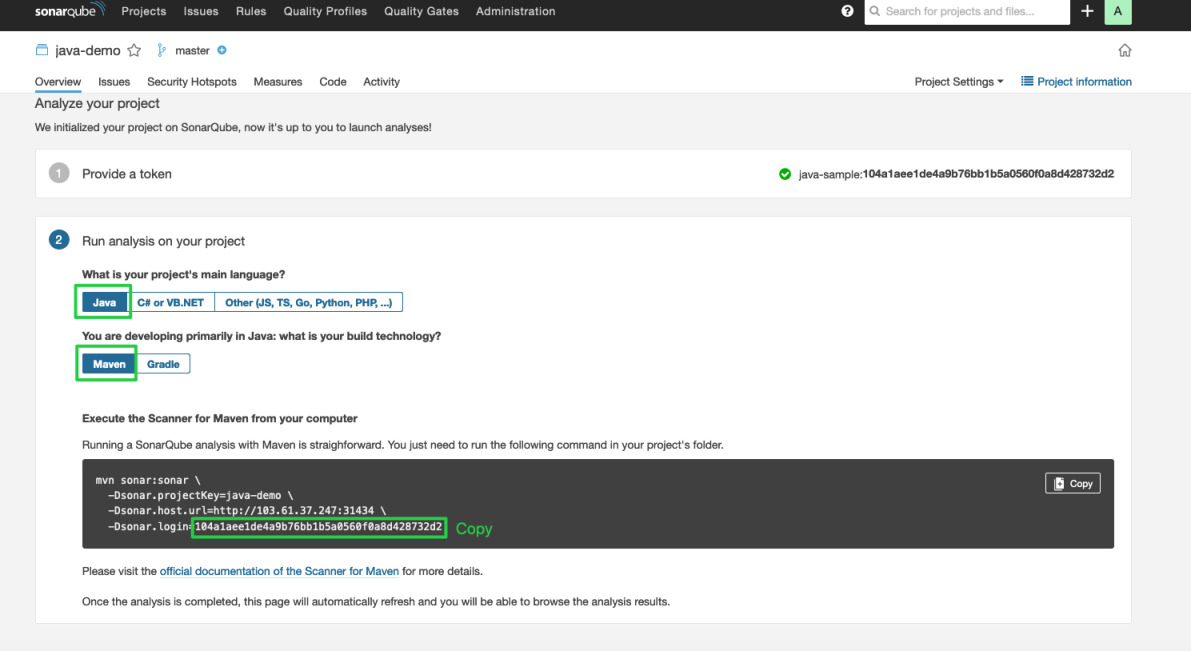
Choose Java and Maven respectively. Copy the serial number within the green box in the image below, which needs to be added in the Credentials section if it is to be used in pipelines.
View Results on the KubeSphere Console
After you create a pipeline using the graphical editing panel or create a pipeline using a Jenkinsfile, you can view the result of code quality analysis.
Feedback
Was this page Helpful?
Receive the latest news, articles and updates from KubeSphere
Thanks for the feedback. If you have a specific question about how to use KubeSphere, ask it on Slack. Open an issue in the GitHub repo if you want to report a problem or suggest an improvement.












 Previous
Previous
